|
Technologies
The key technologies used in wireless LAN systems include Ethernet data networking, spread spectrum radio transmission, and security processes.
Ethernet Ethernet is a packet based data transmission system that is primarily used in local area networks (LANs). Ethernet is the core technology used for wired and wireless 802 LAN systems. The use of common Ethernet technology allows for simple integration of wireless and wired LAN systems.
Ethernet is the common name for the IEEE 802.3 industry specification and it is often characterized by its data transmission rate and type of transmission medium (e.g., twisted pair is T and fiber is F).
Ethernet systems in 1972 operated at 1 Mbps and became standardized by the IEEE in 1985 as 802.3 . In 1992, Ethernet progressed to 10 Mbps data transfer speed (called 10 BaseT). By 1995, Ethernet data transfer rates increased to 100 Mbps (100 BaseT) and in 1998, 1 Gbps (1000 Base T) was introduced. In the year 2000, 10 Gigabit fiber Ethernet prototypes had been demonstrated.
The Ethernet system is composed of multiple layers of communication processes called protocol layers. Each layer has a specific set of rules (protocols) to follow. Because each layer in the Ethernet system knows how the other layers are supposed to operate, each layer is essentially independent from each other.
Ethernet systems have three key layers; the logical link control (LLC) data link layer, medium access control (MAC) sub layer, and multiple types of physical layers. Ethernet transmission can be provided on twisted pair, coaxial cable, wireless, or fiber cable. In 2001, the common wired connections for Ethernet was 10 Mbps or 100 Mbps. 100 Mbps Ethernet (100 BaseT) systems are also called “Fast Ethernet.” Ethernet systems that can transmit at 1 Gbps (1 Gbps = 1 thousand Mbps) or more are called “Gigabit Ethernet.” In 2003, wireless Ethernet data transmission rates ranged from 2 Mbps to 54 Mbps.
Originally created by an alliance between Digital Equipment Corporation, Intel and Xerox, Ethernet DIX, is slightly different than IEEE 802.3. In Ethernet the packet header includes a type field and the length of the packet is determined by detection. In the IEEE 802.3 specification, the packet header includes a length field and the packet type is encapsulated in an IEEE 802.2 link layer header. Most modern day “Ethernet” devices are capable of using both protocol variations, however, older equipment was not able to do this.
Figure_WALN_6 shows a typical Ethernet system. This diagram shows an Ethernet system that has 2 data rates: 10 Mbps and 100 Mbps. This system interconnects two different data rate Ethernet systems using a bridge. The bridge temporary stores (buffers) and retransmits Ethernet data frames when it recognizes the Ethernet addresses that are associated with the networks that it is connected to. It also connects the Ethernet systems to out- side networks using a router. The router converts the Ethernet device address to other addresses (such as IP) that can be routed to other networks.
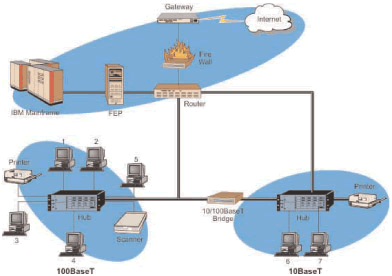
Figure_WALN_6: Ethernet System
Spread Spectrum Radio
Spread spectrum radio transmission is a process of spreading information signals (typically digital signals) so the frequency bandwidth of the radio channel is much larger than the original information bandwidth.
To create a spread spectrum signal, the information signal is multiplied by a spreading code. The multiplication process produces several bits of information for each bit of information signal. This makes the transmitted signal over a wide frequency band. To receive the signal, the spread spectrum receiver must use the same spreading code to recover the original information signal.
This technique changes the frequency components of a narrowband signal so they are spread over a relatively wide frequency band. The resulting signal resembles electrical noise (called white noise).
Spread spectrum transmission is a technique that has been used to achieve very high signal security and privacy, and to enable the use of a common frequency band by many users. This is because the transmitted signal energy is relatively low compared to the natural background noise of received signals. Because the signal is spread over such as wide band, other narrowband signals (such as a high power radio jamming signal) have little effect on the overall transmission of the spread spectrum signal. This makes the spread spectrum signal very hard to find and very hard to interfere with.
Figure_WALN_7 shows how spread spectrum transmission operates. In this example, a data file is being transferred from a computer to a WLAN card at 2 Mbps. Each bit of the 2 Mbps data is multiplied by a 10 bit spreading code. For each logic bit in (logic 1 or a logic 0), 10 new bits are produced. This results in a new data rate of 20 Mbps. This 20 Mbps signal is provided to a binary shift keying modulator that creates a 20 MHz wide radio signal (1 bit = 1 Hz). This 20 MHz wide radio signal is received and demodulated by a WLAN card to produce the 20 Mbps data signal. This data signal is provided to a correlator that compares the data to the same 10 bit code that was used to spread the original signal. If a majority of the bits correlate (match) to the original signal, the output data signal is produced. Notice in this example that if some of the spreading bits are received in error, a majority of the code gets through and this produces the correct information bit.
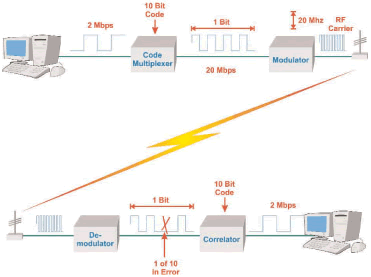
Figure_WALN_7: Spread Spectrum Transmission
Modulation Types Modulation is the process of changing the amplitude, frequency, or phase of a radio frequency carrier signal (a carrier) to change with the information signal (such as voice or data). The 802.11 systems use multiple types of digital modulation. The modulation types used in 802.11 systems have transitioned from simple Gaussian Frequency Shift Keying (GFSK) modulation used in the original 802.11 system to Orthogonal Frequency Division Multiplexing (OFDM) used in the 802.11g system.
Figure_WALN_8 shows different basic forms of digital modulation. This diagram shows ASK modulation that turns the carrier signal on and off with the digital signal. FSK modulation shifts the frequency of the carrier signal according to the on and off levels of the digital information signal. The phase shift modulator changes the phase of the carrier signal in accordance with the digital information signal. This diagram also shows that advanced forms of modulation such as QAM can combine amplitude and phase of digital signals.
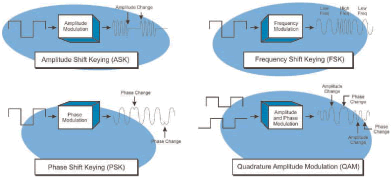
Figure_WALN_8: Digital Modulation Types In general, the more efficient (data transmission capacity) the modulation type, the more complex (precise) the modulation process is. The more precise the modulation process (smaller changes represent digital bits), the more sensitive the modulation is to distortion or interference. This usually means that as the data transmission rate increases, this increases the sensitivity to interference. To help manage this process and ensure the maximum data transmission rate possible, 802.11 systems automatically change their data modulation types and data transmission rates (autorate) based on the ability of the channel to transfer data. The 802.11 systems will usually try to send information at the highest data transmission rate possible. If the data transmission rate cannot be maintained, the 802.11 systems will attempt to transmit at the next lower data transmission rate. Lower data transmission rates generally use a less complex (more robust) modulation type.
Access Security Access security is the process of restricting access rights and protection the transfer of information from unauthorized users. The security of information can be divided into three key levels; physical access, account authorization, and encryption. Having the ability to secure data in WLAN systems is important, as it is usually easy to gain physical access to transmitted information in a WLAN system. While it may be easy for unauthorized users to gain physical access to the transmitted signal, they may not be able to find and acquire the actual information signal (this is not easy for low power mobile devices). If they are able to detect and decode the signal, they may have to pass through a level of authentication to gain access to system resources. If they can pass through the authorization of services (some systems may not have any security set), the data may be encrypted which renders it useless to most eavesdroppers.
While WLAN systems are relatively easy to setup and use, security settings must be established to prevent unauthorized access and control. The use of WLAN systems without authentication or encryption security permits unauthorized access and possible hijacking of established communication links.
WLAN systems may also be setup to allow wireless Roaming. Wireless roaming provides users with the ability to connect to different ISPs with a single user account. Visiting users may be screened to determine if they have valid account codes.
A desirable feature for some WLAN systems is to allow direct networking (called “Adhoc” networking) between communication devices without the need to use an access port. Adhoc networking may not have security settings established. Users should be aware how to setup security settings for adhoc users (adding encryption passcodes).
Physical access is the ability for someone to capture or insert information into a communication system. Some local area wireless communication systems such as wireless LANs operate at a fixed location on a predefined frequency band for extended periods of time. This allows nearby eavesdroppers to capture a portion of the radio signal using fairly low cost (e.g. Pringles can) directional antennas. Therefore it must be assumed that the physical reception of a WLAN or WPAN signal is possible and if the information is valuable (such as cash register sales), it more likely to occur.
Figure_WALN_9 shows that some WLAN systems usually have fixed locations such as in retail stores. Because WLAN systems use relatively high power (possibly 1 Watt), eavesdroppers may use direction (high-gain) antennas at a remote location to gain physical access to the WLAN radio signal.
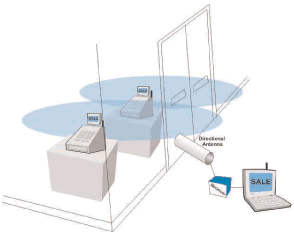
Figure_WALN_9: Wireless LAN Physical Security Identity validation (also called authentication) is the reliable identification of a requesting user and determining what resources (authorized services) the user is allowed to have access to transmission and network resources. Authorization usually involves sharing some predetermined information between a potential user (client) and an information provider (server).
To help maintain the security of systems, authentication of both devices (mutual authentication) may be required. Mutual authentication is the process of each device in a communication session authenticating the other device.
Unauthorized users (hackers) use various processes or techniques to attempt to gain access to services. These users may attack the access the system through the systematic process of incrementing the password characters and repeatedly attempt access with new passwords. Another process for hacking into systems is through the use of dictionary attacks that cycling through a dictionary of words, names, or possible password codes to gain access to a communication system.
There are several protocols that can be used to provide authentication such as Extensible Authentication Protocol (EAP) or Remote Access Dial In User Server (RADIUS). Some of the authentication processes and devices such as GSM SIM cards may be integrated with WLAN systems.
Radius authentication receives identification information from a potential user of a network service, authenticates the identity of the user, validates the authorization to use the requested service, and creates event information for accounting purposes. To standardize the authorization process, RADIUS protocol was developed and is specified in RFC's 2138 and 2139, RADIUS is a client/server protocol that uses simple user datagram protocol (UDP).
Figure_WALN_10 shows a typical authentication process used in a WLAN system. In this diagram, two wireless data terminals each share a secret key. When one of the devices wants to authenticate the other device (roles can also be reversed), it sends an authentication request and a random number. This random number is used by the receiving device and is processed with the secret key with an authentication (data processing) algorithm to produce a result. This result is sent to the originator. The originator uses the random number it sent along with its secret key to calculate a result. If the result received from the remote device with its own result matches, the authentication passes. Note that the secret key is not sent on the radio channel and that the result will change each time the random number changes.
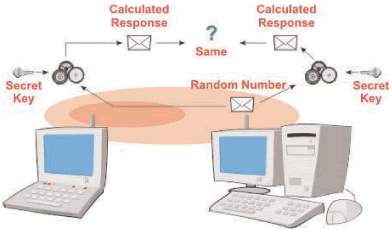
Figure_WALN_10: Wireless LAN Authentication
Encryption (Information Privacy) Encryption is a process of a protecting voice or data information from being obtained by unauthorized users. Encryption involves the use of a data processing algorithm (formula program) that uses one or more secret keys that both the sender and receiver of the information use to encrypt and decrypt the information. Without the encryption algorithm and key(s), unauthorized listeners cannot decode the message. When the encryption and decryption keys are the same, the encryption process is known as symmetrical encryption. When different encryption and decryption keys are used (such as in a public encryption system), the process is known as asymmetrical encryption. The encryption key for the 802.11 systems can be composed of alphanumeric characters (letters and/or numbers).
There are two forms of encryption used in 802.11 system; wired equivalent privacy (WEP) and Wi-Fi protected access (WPA). WEP use a WEP Encryption 40, 64, or 128-bit encryption key to encode the data between the end-user device (station) and the access point (AP).
Figure_WALN_11 shows how encryption can convert non-secure information (clear text) into a format (cyphertext) that is difficult or impossible for a recipient to understand without the proper decoding keys. In this example, data is provided to an encryption processing assembly that modifies the data signal using an encryption key. This diagram also shows that additional (optional) information such as a frame count or random number may be used along with the encryption key to provide better information encryption protection.
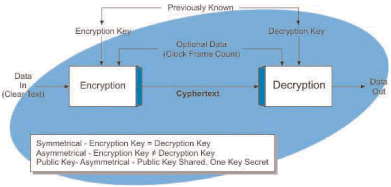
Figure_WALN_11: Data Encryption Longer encryption keys generally offer more information security. The encryption of information adds to the signal processing requirements and transmission delay. Because of national security (some governments want to have the ability to break the security key codes), some countries restrict the use, export or import of products that contain strong encryption capabilities.
It has been demonstrated that the security of WEP is not sufficient for all users. To increase information security, WEP algorithm is being replaced with Wi-Fi Protected Access (WPA). WPA is an early implementation of the 802.11i industry standard.
WPA uses Temporal Key Integrity Protocol (TKIP) for encryption. Access to the network starts with locally authenticating the requesting user before allowing connection to the wired network. The WPA process starts with a pre-shared key is similar to the pass phrase key used in WEP. However, unlike WEP, a new key is generated each time the device associates with the AP.
It may be possible to upgrade products after their purchase to have WPA encryption capability. This upgrade will likely be performed by a firmware software download via the Internet.
“Ethernet,” Jon Dron, http://edtech.it.bton.ac.uk/ism05-01/ethernet/ethernet.htm, 24 September, 2001
|

